Encryption
symmetric vs asymmetric
24 Mar 2018
View Comments
#computer
#programming
#cryptographic
#algorithm
#scheme
#security
#RSA
#AES
 |
In the past, encryptions were simple. Well, there weren’t many places where people need complex encryption for communication because communication methods were pretty much limited, by voice or letters. People sent and received encrypted letters where no one can steal and see what the letters mean unless it gets to the destined person who would decrypt what it says in the letter. Here is a famous ancient example of Julius Caesar. One day he sent messages to his generals, he didn’t trust his messengers. So he replaced every A in his messages with a D, every B with an E, and so on through the alphabet. Only someone who knew the “shift by 3” rule could decipher his messages.
Ages later in 1960s, usage of computers started to become quite popular. As computers develop, communication took to the whole another level. Computers quickly adapted to communicate in various protocols. Each of these protocols required secured connection to safely communicate without any breaches. There needed a standard way to communicate securely between 2 or more computers.
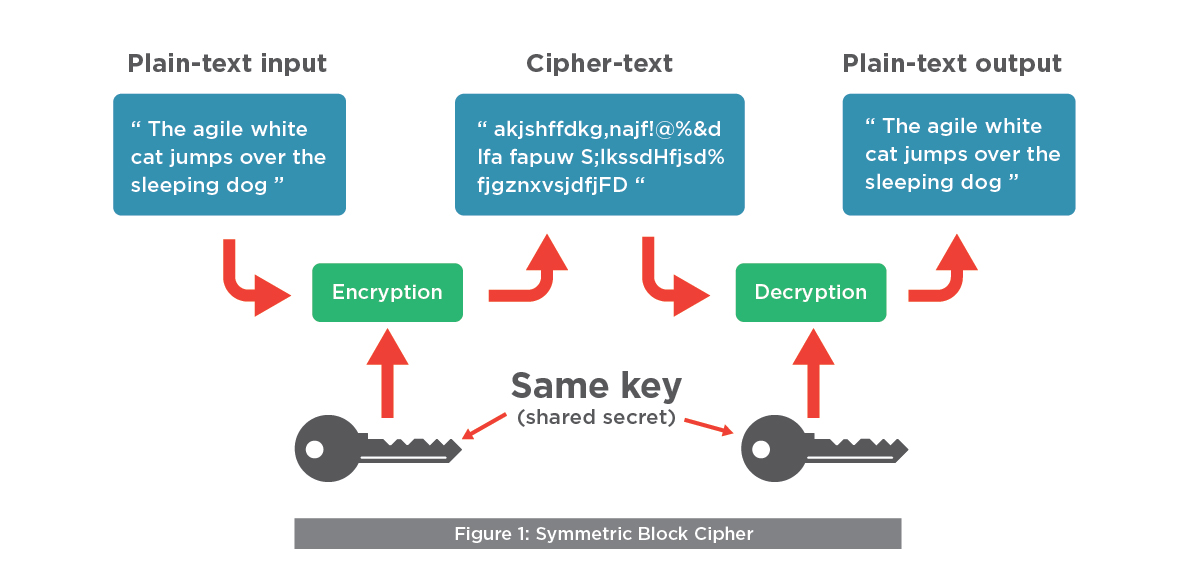 |
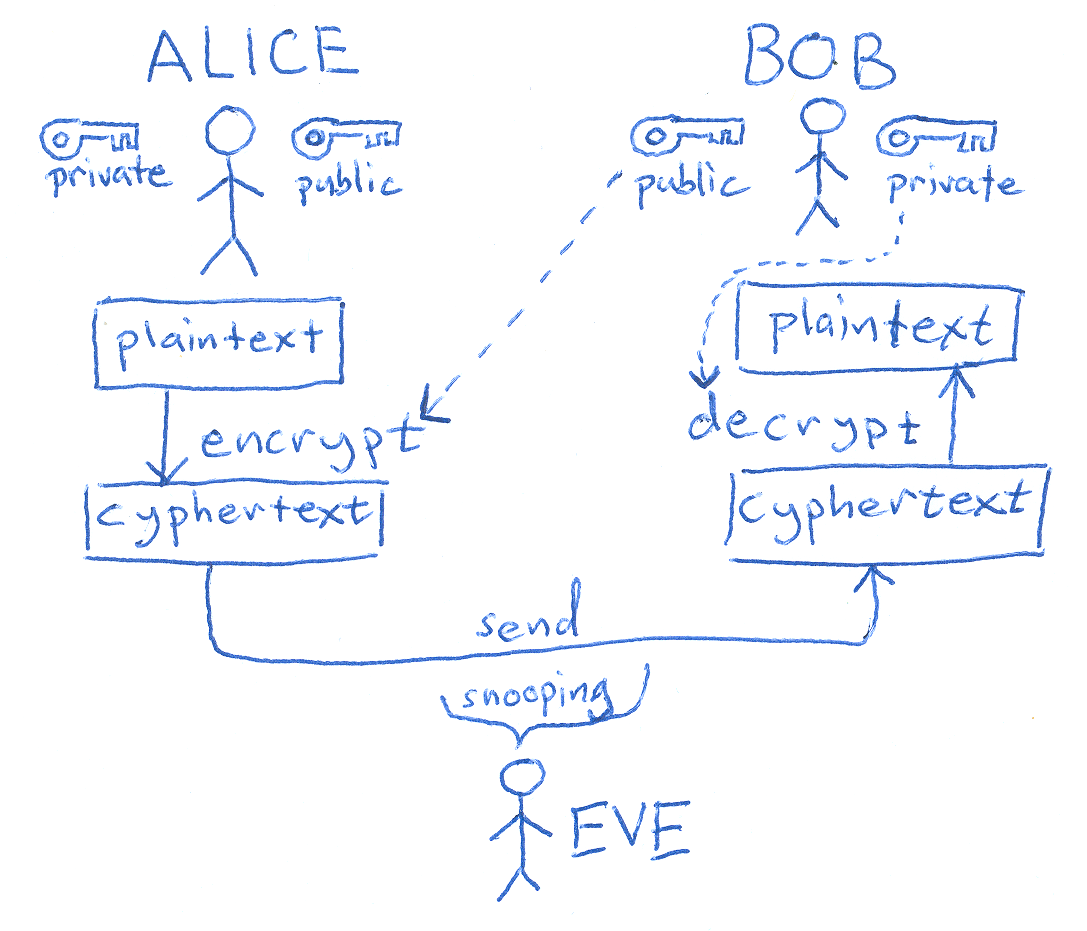
We typically divide encryptions into 2 different kinds, symmetric and asymmetric. In symmetric encryption, both sides must have the same secret key (password) for encrypting/ decrypting a message. In contrast, asymmetric encryption requires the public key which is the key available to anyone to encrypt a message. Then there is a private key (secret key) which can be used to decrypt the encrypted message (using the public key). Those public and private keys for an asymmetric cryptographic algorithm would likely be generated at the same time. The most popular symmetric key algorithm used today is AES (Also known as Rijndael). For the asymmetric key algorithm, RSA is probably the most common ones used today.
 |
When you read through the algorithms, AES might appear more secure than RSA. However, RSA can bump up the security level by increasing the modulus. This would lag the processing of encryption/decryption of RSA though. You essentially need to find the balance between performance and security, yet again.
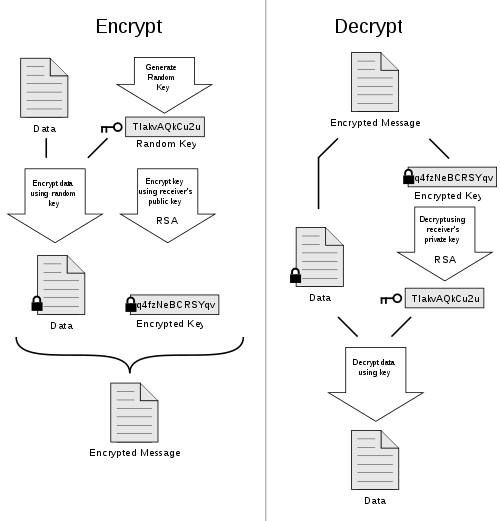
In late 2016, I wrote a blog post about the keybase.io. Keybase works mainly as web identifier but they also offer a good communication platform to send/receive encrypted messages. They use an algorithm called, PGP which stands for “Pretty Good Privacy”. This hybrid algorithm uses both symmetric and asymmetric encryption to encrypt its message. Also, there are added benefits using the algorithms such as data compression and digital signatures.
 |
Obviously, there are many more encryption ciphers than these 3. Above 3 describes fairly well for distinct kind of the ciphers. Encryptions involve mathematics quite heavily but upon reading how each algorithms work, they are really clever and interesting. This blog post covers basic cryptographic algorithms, not the protocols. Protocols may be using these ciphers to employ their security aspects for certain actions.
