Proxy and VPN
What are the differences?
24 Jan 2018
View Comments
#proxy
#VPN
#computers
#network
Both a proxy and a virtual private network (VPN) services are destined to re-route your internet traffics which would eventually update (mask) your IP. However, the 2 services’ functionalities are slightly different. Let’s take a look at the contrasts and compare the behaviours of these 2 network services.
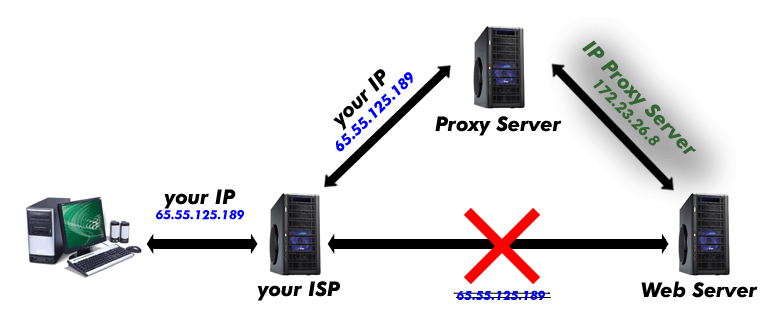 |
In a general computer network, a “proxy” typically refers to a network service which uses a server that acts as an intermediary (server in the middle) for web communication. Although proxies could be used for different purposes, in most cases, the proxy can simply be thought as a “web filter” because the majority proxies are focused on the “web” activities (web proxies). For example, you do not wish the web servers sniffing around you on your identity information such as location information, ISP information, IP address, etc. The “proxy” may be used for these cases because the proxy server would re-route your requests to the destination for you which would prevent the web servers from sniffing this information out of you. You can also use it to bypass some of the blocked contents by making yourself anonymous.
There are 2 generally known types of proxy servers, forward proxy and reverse proxy. The forward proxy would simply forward the requests received from the client to the destination and relay the response to the client back. However, for reverse proxy servers, once they have acquired the requests, they could and probably would manipulate the destination information to get to the appropriate destination. So normally in reverse proxy setting, proxy servers are coupled with the actual web destination server since it holds the purpose of delivering the requests to the correct destination.
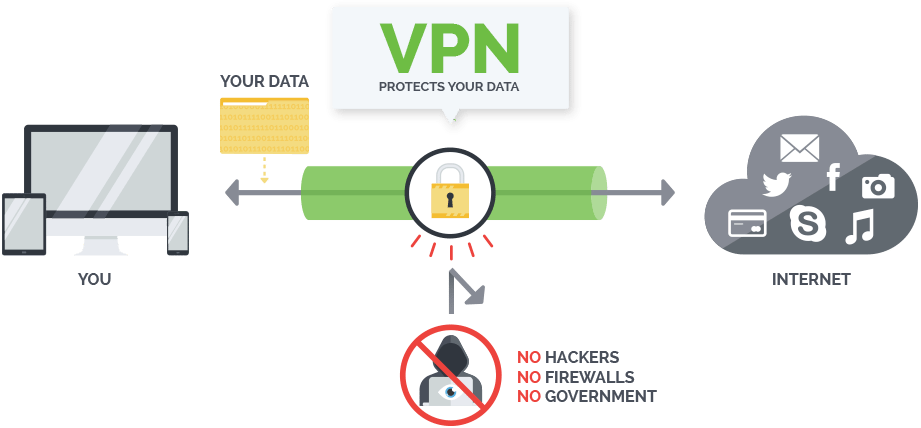 |
A virtual private network (VPN) in the other hands have totally different concepts of masking. It extends a private network across the public network which enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. We would typically call this making a secure “tunnel” in VPN terminology. The important piece to understand here is that all traffic are “encrypted”. Therefore, none of the middlewares (including your ISP/hackers) could fetch your valuable information. Here is an example of what TELUS (my ISP) would be collecting. In my opinion, TELUS is not an aggressive collector compared to some of the other ISPs I’ve seen. These pieces of information are basic ones that majority of ISP would collect:
- Account and service information: such as your name, address, email, telephone number, credit card or bank information for pre-authorized payments
- Details of the products and services you receive from ISP: such as your wireless device rate plan or Optik TV channel subscriptions.
- Network performance and usage information: For example, we will note your wireless device location for specific uses, such as when you dial 911 and we provide GPS and triangulation data to the 911 operations centre. Or if we’ve had an unexpected TV channel outage, we might examine who was watching a particular channel at the time in order to issue an apology credit.
To be fair, similar to the proxy, the VPN can also be easily connected or disconnected with the click of a button on your desktop. The key difference between the two would be that proxy servers in majority time are “browser-based” where the traffics would get re-routed by an intermediary server. However, a VPN works with entire “internet-based” services (not just browser). However, VPN may give you trouble because your ISP can choose to filter out the connection. In a VPN network, the computers at each end of the tunnel encrypt the data entering the tunnel and decrypt it at the other end. However, a VPN needs more than just a pair of keys to apply encryption. That’s where protocols come in. A site-to-site VPN could use either Internet protocol security protocol (IPSec) or generic routing encapsulation (GRE).
Conclusion
I would just think of the differences in this fashion:
- Proxy: “browser-based”, intermedia server to re-route your requests to hide information about you.
- VPN: “internet-based”, secure encrypted data communication with the destination
